Verify Specops Password Policy License Usage
*This article applies to version 7.11 or later*
This article will review how Specops Password Policy affected/subscription licenses are consumed and assumes you are on the latest version of Password Policy.
Both affected (perpetual) and subscription licenses use the same model to count licenses — the count is based on the number of enabled Active Directory user objects that have a Specops Password Policy GPO applied to them in Active Directory.
License usage will be displayed in the Password Policy Domain Administration tool. Launch the tool, confirm the correct domain is selected (if applicable) and view current license usage from this view.
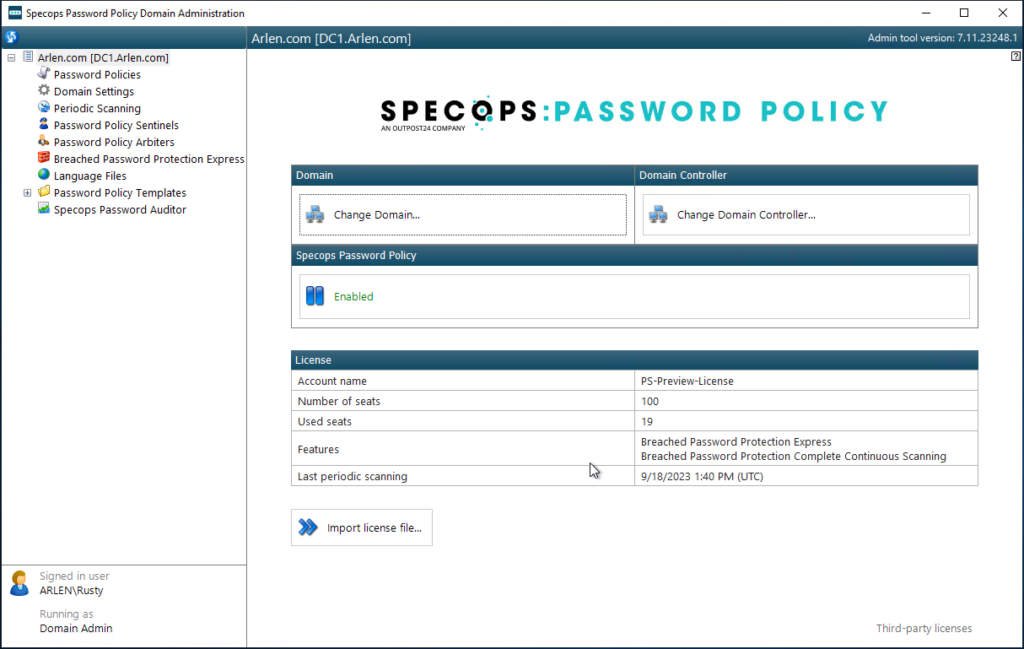
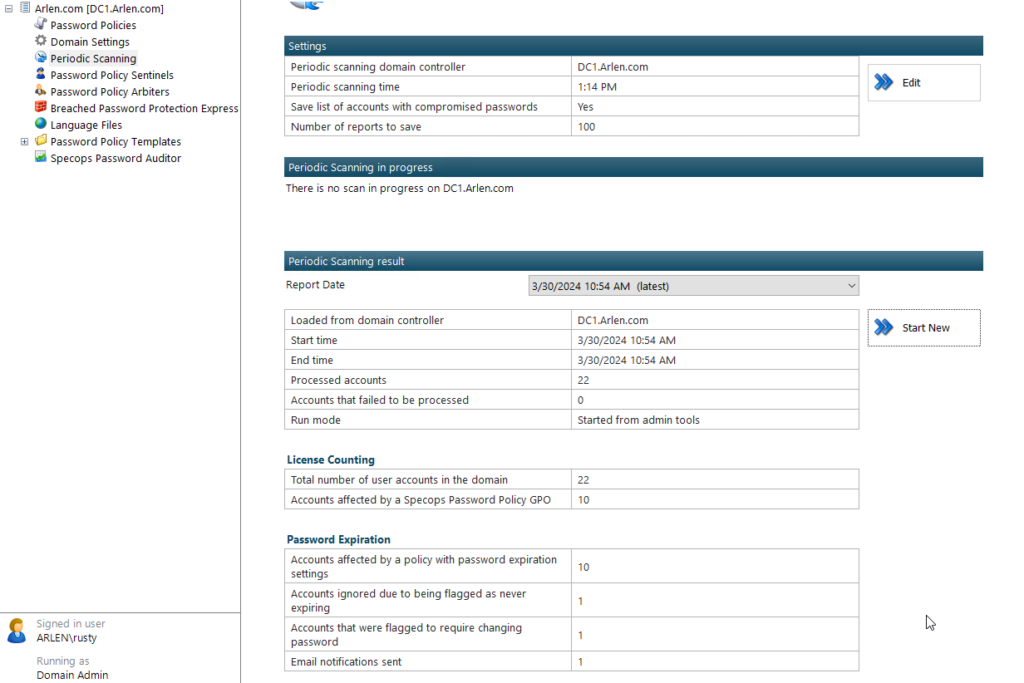
Specops Password Policy regularly updates a record of how many licenses have been consumed. The license check is part of the periodic scanning process performed by the Password Policy Sentinel Service installed on the domain controller holding the PDC Emulator Role. The current license consumption details will be logged under the periodic scanning tab:
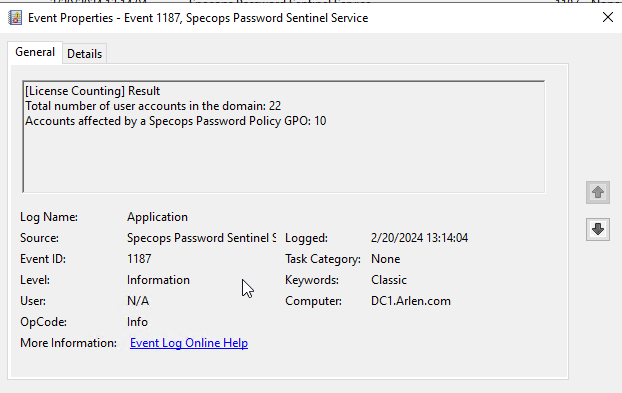
It can also be found in the Event Viewer under the Windows Application with event ID 1187.
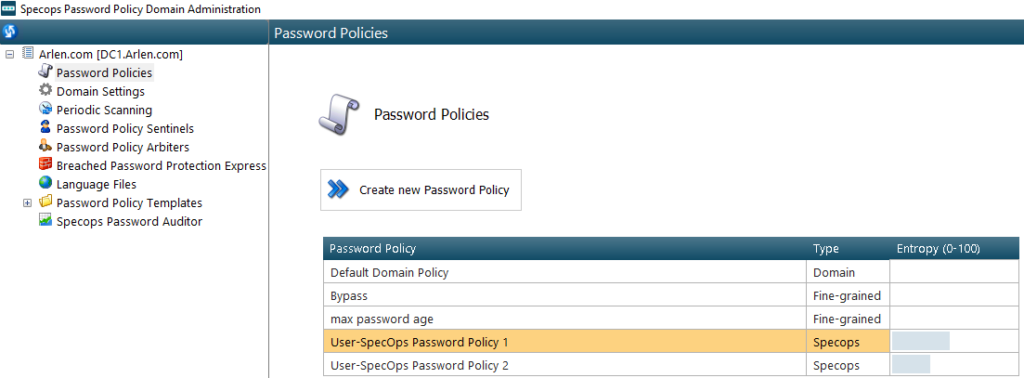
Adjusting License Consumption
If license counts are higher than expected, you may need to adjust the scope of your Password Policy GPOs to exclude some user objects in order to reclaim licenses for those users. Begin by checking which GPOs in your domain contain Password Policy settings. On a system with the Password Policy Admin Tools installed, launch Password Policy Domain Administration from the start menu and got to the Password Policies section. GPOs containing Specops Password Policy settings will be listed in the Group Policies section on the right.
To determine how each Specops Password Policy GPO is applied we must check in Group Policy Management Console MMC. Check the locations where the GPO is linked and whether any Security Filtering has been applied. The default is authenticated users:
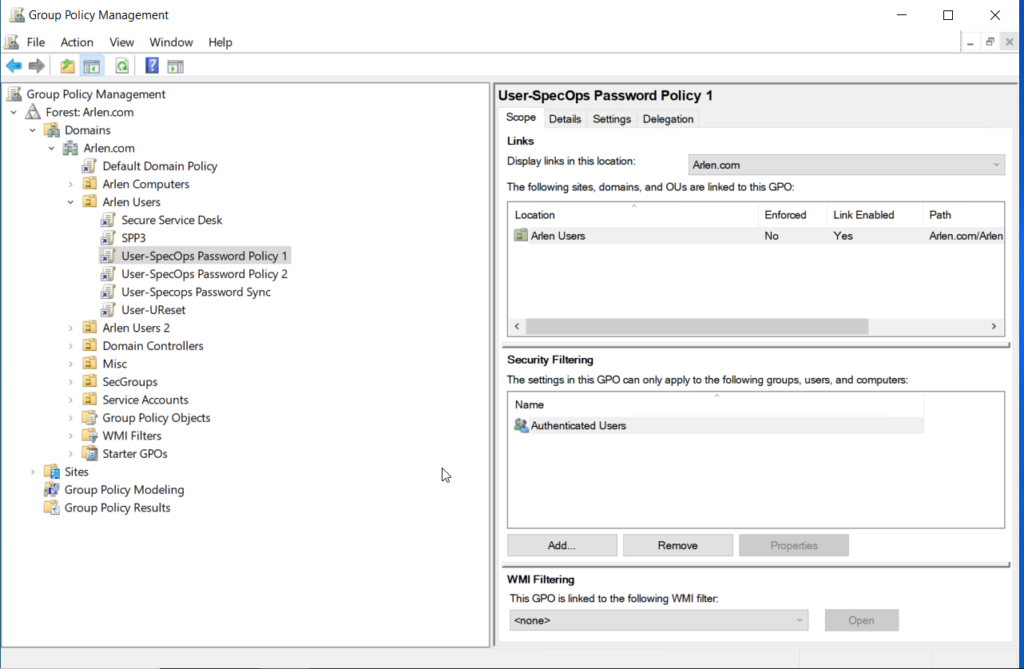
In order to reduce license consumption any of the following changes can be made:
- Link the GPO on different sub-OUs and disable/delete the current links
- Deny applying the GPO to a security group via advanced delegation on the GPO
Change the Security Filtering to limit the GPO’s scope to a security group
If you are applying the GPO to the root or a large scope and want to filter by security group, do the following:
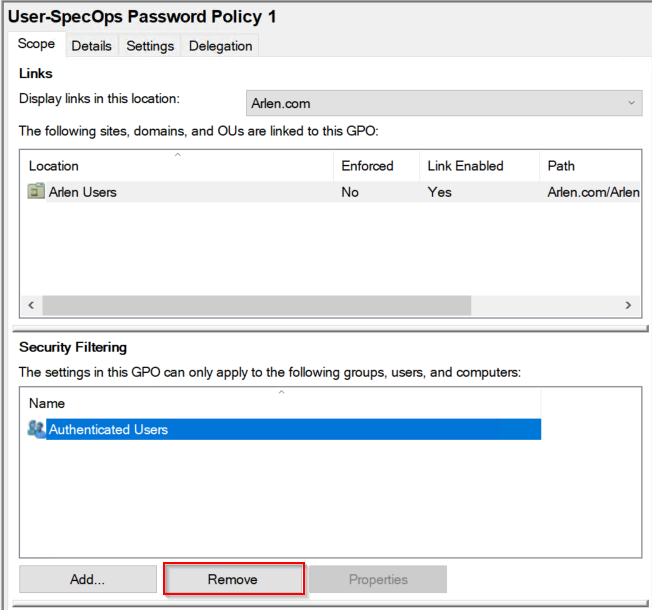
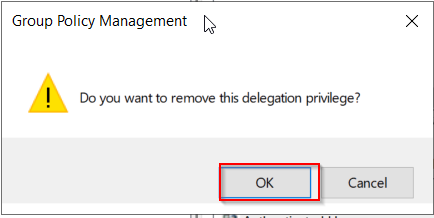
Then add the desired security group:

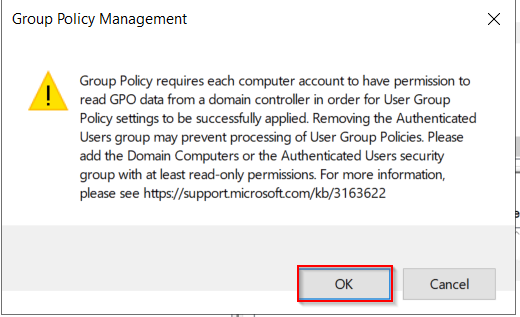
Then switch to the Delegation Tab and Add Switch to the delegation tab and add authenticated users with read access:
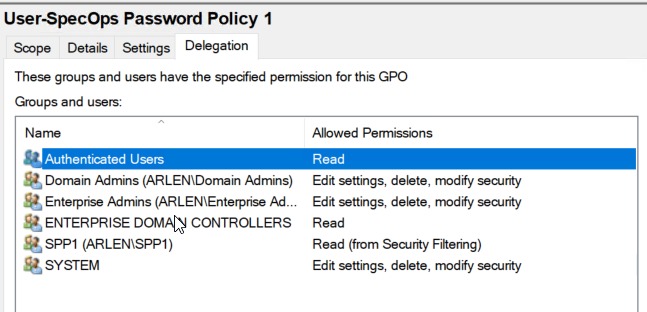
Once changes are made, the user counting data in Password Policy will not update until the next daily user count. If you would like to see results immediately you can also count consumed licenses manually by using the Active Directory and Password Policy PowerShell modules. Password Policy version 7.2 or later is required for these commands:
Get-ADUser -filter { enabled -eq $true } | % { Get-PasswordPolicyAffectingUser $_ } | Measure-ObjectAdd a searchBase parameter and specify the distinguishedName of an OU to count license only for users under that specific OU:
Get-ADUser -SearchBase "OU=Users,DC=domain,DC=com" -filter { enabled -eq $true } | % { Get-PasswordPolicyAffectingUser $_ } | Measure-ObjectIf you want a list of users for a specific OU:
get-aduser -searchbase "OU=Demo Users,DC=demo,DC=local" -filter { enabled -eq $true} | select sAMAccountName, @{ Name = 'SPP_Policy'; Expression = { $(get-passwordpolicyaffectinguser $_.sAMAccountName).GPOname }}If you would like the entire domain:
get-aduser -filter { enabled -eq $true} | select sAMAccountName, @{ Name = 'SPP_Policy'; Expression = { $(get-passwordpolicyaffectinguser $_.sAMAccountName).GPOname }}