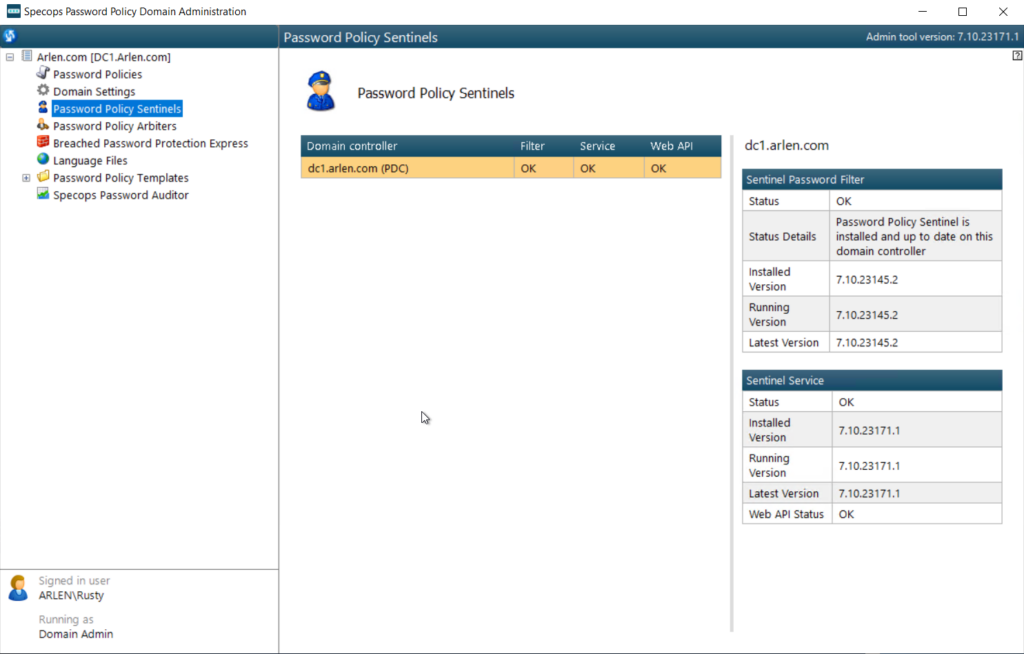
Verify Sentinel Installation State
This article will review the steps required to confirm the Specops Password Policy Sentinel is installed properly on your domain controllers. The Sentinel is required on every writeable domain controller in order to ensure proper enforcement of Specops password policies. It does not need to be installed on read-only domain controllers; if you have any read-only domain controllers in your environment they are not displayed in the Password Policy admin tools. Verifying the Sentinel State is an important step in troubleshooting if you suspect Specops Password Policy rules are not being enforced, or for auditing that the environment is fully compliant with regard to enforcement of Password Policy rules.
Check Sentinel State on all Domain Controllers
You can use the Password Policy Domain Administration tool or accompanying PowerShell module to query all domain controllers in the domain and the state of the Sentinel on each of them. Each domain controller will be listed, along with both the installed and running version numbers.
If the installed version if populated and running version is either blank or at a lower revision than the installed version, this indicates the Sentinel was installed but the domain controller has not yet been rebooted to complete the installation to load the installed Sentinel in memory.
The same report can be run via PowerShell on a machine with the Password Policy Domain Admin tools installed (the Admin tools do support Server Core) using the Get-PasswordPolicySentinel cmdlet:
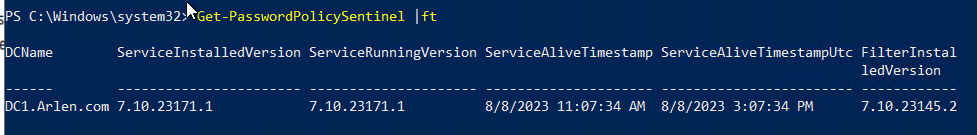
Note: for versions prior to Password Policy 7.4, the RunningVersion and InstallStateResult fields were not available. Specops recommends upgrading to the latest version of Password Policy; if you must verify installation of a Sentinel prior to 7.4 please see the next section on manual verification steps.
Verify Sentinel Installation on a Single Domain Controller
In this section we will walk through some steps to confirm installation and operation of the Sentinel on a domain controller using only native Windows/AD operations.
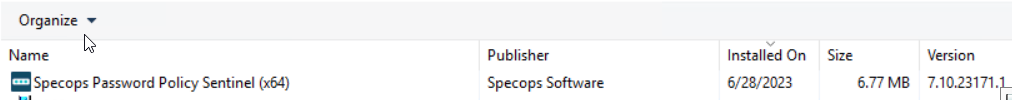
Verify the Sentinel MSI Is Installed
Check for the Sentinel in Control Panel Programs and Features, or for Server Core installations through comparable WMI/PowerShell queries:
For Server Core installations or scripting purposes, use PowerShell to query the registry:
Get-ItemProperty HKLM:\Software\Microsoft\Windows\CurrentVersion\Uninstall\* | where {$_.displayname -like "*Sentinel*"} |select Displayname,DisplayVersion,Publisher,InstallDate | fl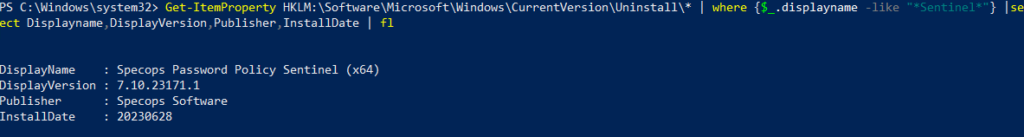
Verify the Domain Controller was Rebooted Since Sentinel Installation
Check the system boot time using WMI/PowerShell:
Get-CimInstance -ClassName win32_operatingsystem | select lastbootuptime
Compare the boot time to the installed date from the previous section to ensure the domain controller was rebooted since the Sentinel MSI was installed. If both events were on the same date the result is ambiguous (Windows only records the date the MSI was installed not the exact timestamp) so we must dig deeper. Check the Windows Application Event Log for event source Specops Password Policy Sentinel and ID 1073, which is logged by every Sentinel once every 24 hours:
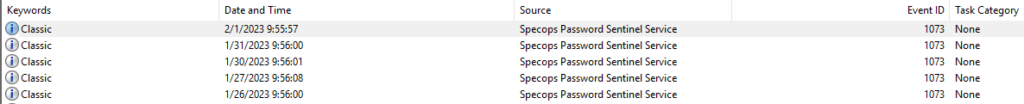
Using PowerShell:
Get-WinEvent -filterhashtable @{
logName='Application'
ProviderName='Specops Password Sentinel Service'
ID='1073'
}If results are returned with at least this one event every 24 hours, the Sentinel is installed properly.
If both the installed dates and boot times are today we expect there are no events logged yet. Confirm the exact time the MSI was installed by searching the event logs using PowerShell:
Get-WinEvent -filterhashtable @{
logName='Application'
ProviderName='MsiInstaller'
Id='1033'
}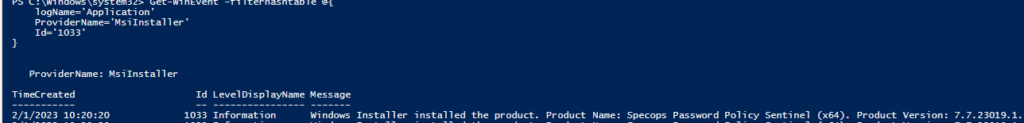
If this event timestamp is after the last boot time, reboot.
