This website uses cookies to ensure you get the best experience on our website. Learn more

Marcus White
Marcus is a Specops cybersecurity specialist based in the UK. He’s been in the B2B technology sector for 8+ years and has worked closely with products in email security, data loss prevention, endpoint security, and identity and access management.
Articles written by Marcus White
-
Jul
03
Kerberoasting attacks: How to keep your Active Directory safe
A domain administrator account is the holy grail of privileged accounts in a Microsoft Active Directory environment. If an attacker can get their hands on a Domain Administrator account in the domain, they’ll have access to basically everything. Kerberoasting is…
Read More -
Jun
26
Active Directory password hardening: How it’s done
Weak passwords are a problem waiting to happen – Verizon estimates that 80% of hacking-related breaches come from weak or stolen passwords. They’re the most common way for people to access their accounts and applications, making them an obvious attack…
Read More -
Jun
22

MFA prompt bombing: How it works and how to stop it
User credentials are golden prizes for attackers. Weak or breached credentials provide an easy target for attackers looking to log in to a network instead of breaking in. Most businesses have caught on to the fact that multi-factor authentication (MFA)…
Read More -
Jun
13
Six ways to apply the principle of least privilege to your Active Directory
The principle of least privilege is simple but important: it states that users only have the minimum access necessary to perform their job. For organizations using Active Directory (over 90% of the Fortune 100), this means the minimum necessary permissions…
Read More -
May
23

Guide to the PCI-DSS v4.0.1 regulations [Updated for 2025]
The PCI DSS compliance framework has been a staple in the cybersecurity realm for businesses handling credit card transactions. The Payment Card Industry Data Security Standard was developed to encourage and enhance payment card account data security. It helps define consistent security measures…
Read More -
Jan
24

Zero to hero: How zero-trust models protect against cyber-attacks
Perimeter-based security models were built for a world where corporate networks had clear boundaries—but that world no longer exists. Modern enterprises operate in hybrid environments with cloud services, remote workforces, and third-party integrations, creating countless entry points for attackers. The…
Read More -
Oct
12
How to configure the NCSC password list in AD
Passwords are one of the weakest links when it comes to ensuring that your environment is secure. Traditional user accounts and the associated passwords have long been the default security mechanism found in most environments. With the very advanced and…
Read More -
Sep
23
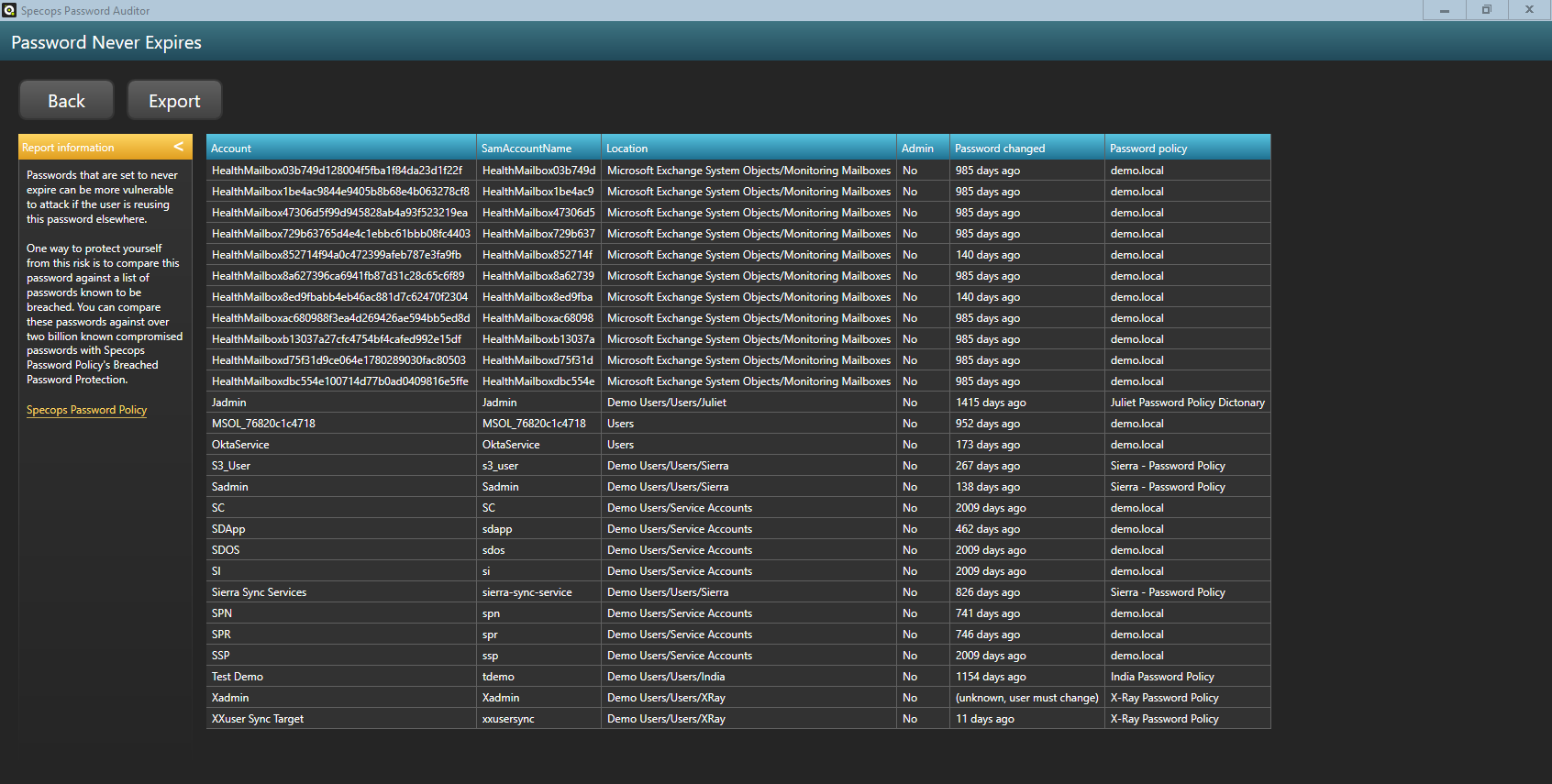
Finding Active Directory passwords set to never expire
Passwords set to never expire can be a security vulnerability for your network. Here is how to to find Active Directory (AD) passwords set to never expire. Some regulatory bodies require passwords to expire every 90 days, while others recommend…
Read More -
Jun
03

Which authentication tools are users most comfortable with?
Authentication is the first line of defense in any organization's cybersecurity strategy, but not all authentication tools offer the same level of security, convenience, or scalability. From traditional passwords to advanced biometric and adaptive authentication, businesses must carefully choose the…
Read More -
Nov
19

How to stop different types of password attacks
What makes users and organizations vulnerable to password attacks? A recent study indicates that user’s perceptions of password security might not always match reality. Many of us overestimate the benefits of including digits or special characters in our passwords, and…
Read More
