This website uses cookies to ensure you get the best experience on our website. Learn more
Brandon Lee has been in the industry 20+ years, is a prolific blogger focusing on networking, virtualization, storage, security & cloud, and contributes to the community through various blog posts and technical documentation primarily at Virtualizationhowto.com.
Articles written by Brandon Lee
-
Jul
07

Are password reset solutions still relevant?
In case you haven’t been keeping up with the latest password guidance from noted cybersecurity organizations, it has changed from the traditional advice given regarding password security and password security policies. There are new and better ways to protect and secure account passwords than legacy…
Read More -
Jun
21

What is the NCSC guidance on password managers?
To keep our accounts secure across the multiple services that we use, we need to choose strong passwords that are unique for each account or service. Yet, 52% of people reuse the same password for multiple accounts. Remembering multiple strong passwords for perhaps dozens of accounts is…
Read More -
Jun
15

HIPAA compliant password manager
Compliance with industry regulations are extremely important to IT priorities, and cybersecurity. One of the more prominent standards for safeguarding personal data is the Health Insurance Portability and Accountability Act (HIPAA) which provides guidelines for organizations dealing with protected health information (PHI). For sysadmins, compliance with HIPAA requires visibility and technical controls to protect electronic personal health information…
Read More -
Jun
10

What is the NIST guidance on password managers?
Today’s end-users are juggling many sets of credentials for accessing critical business resources. To prevent users from writing-down, reusing, or selecting weak but memorable passwords, businesses are turning to password managers. A password manager is an encrypted database used for storing, retrieving, and generating passwords. Enterprise password managers not only improve password security, but also simplify password management for…
Read More -
May
11
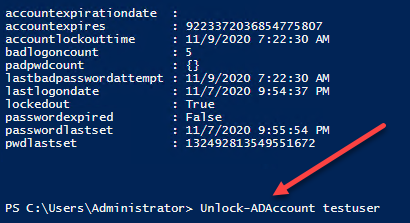
How to check if an AD account is locked out
The Account Lockout Policy in Active Directory Group Policy sets the number of failed sign-in attempts before a user account is locked out. This can be checked with the AD account lockout status. Once the account is locked out, it…
Read More -
Apr
19

HIPAA Security Rule Guidance for passwords
There are an alarming number of cyberattacks targeting the healthcare industry. In October 2020, the FBI released a security warning to hospitals and government agencies of an imminent danger of ransomware attacks. Attackers were said to be targeting healthcare providers…
Read More -
Apr
12

German Federal Office for Information Security password guidance
The German Federal Office for Information Security (Bundesamt für Sicherheit in der Informationstechnik, abbreviated as BSI) is an agency responsible for information security for the German federal government. The BSI is also the central certification body for IT systems. This…
Read More -
Apr
07
CNIL password guidance
Data privacy has become a priority for global businesses due to sweeping regulations such as the General Data Protection Regulation (GDPR). At the same time, other regulatory bodies continue to enforce local data privacy laws. In France, for example, the…
Read More -
Mar
23
Programming your own password filter .dll
Organizations can increase the security of Active Directory passwords by filtering specific passwords from being used in their environment. Password filters help bolster the security protections of Active Directory Password Policy settings by ensuring that end-users cannot use passwords that…
Read More -
Feb
24

NIST Password Reset Guidelines
Passwords are necessary for authentication to different types of technology systems used in businesses today. Yet, they are a dangerous form of information from a security perspective. To strengthen password security, organizations want to take note of password best practices…
Read More

