Specops Authentication is our platform that secures self-service key recovery and password resets, changes and account unlocks with multi-factor authentication (MFA), via self-service and/or at the IT service desk. The platform powers products like Specops uReset, Specops Secure Service Desk and Specops Key... Read More
Authentication
Authentication service outage or compromise? How to keep your business running
User authentication services for MFA impact many systems running in businesses today. But what happens when that authentication service is down or no longer reliable? Planning for the potential pitfalls and challenges in authentication means that your organization won’t... Read More
Zero to hero: How zero-trust models protect against cyber-attacks
Perimeter-based security models were built for a world where corporate networks had clear boundaries—but that world no longer exists. Modern enterprises operate in hybrid environments with cloud services, remote workforces, and third-party integrations, creating countless entry points for attackers.... Read More
How to enforce password complexity in O365?
As organizations move data to the cloud, strong password policies have never been more important. Here is how to use the on-premises Active Directory to enforce password complexity in O365. Read More
CJIS Password Policy Requirements
The Criminal Justice Information Services Division (CJIS) is a division of the FBI that provides a number of tools and services to law enforcement agencies around the country. Through systems like the National Crime Information Center (NCIC), Integrated Automated... Read More
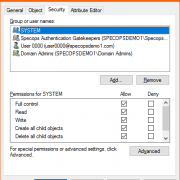
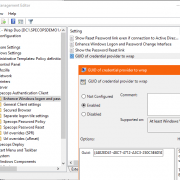
Specops Authentication enrollment data in Active Directory
The Specops Authentication cloud platform is unique in that user data is stored in the customer’s on-prem Active Directory database. Usernames, passwords, and enrollment data/proofs for the various Identity Services provided by Specops Authentication are stored in the customer’s... Read More
Specops Authentication Client and Duo Authentication for Windows Login
The Specops Authentication Client provides enhancements to the Windows logon experience by wrapping the built-in Windows credential provider (GINA). This includes allowing users to reset their passwords from the login screen, as well as enhancing the feedback users receive... Read More
How to stop O365 phishing attacks
O365 phishing attacks are are easy - just trick the recipient into giving up their password on a fake login page. Requiring users to authenticate with additional factors is the best way to stop the attack. Read More
Specops uReset and GDPR compliance
With the introduction of Specops uReset (version 8.1 or later) in the Microsoft EU data center, organizations can now choose which instance of Specops uReset they want to use. Specops uReset is a hybrid password reset solution. The cloud... Read More
Comparing Specops Authentication for O365 and Office 365 MFA: An MVP’s Perspective
In this guest post, Microsoft MVP Nick Cavalancia provides a high-level comparison of how Microsoft and Specops implement MFA for O365, and what it means to the security-conscious organization. Read More